There are many links for this in the Internet so I am not going to discover the fire but I struggled a bit so….
The official links from github were ok and other people did a very good job too documenting the process.
https://docs.github.com/en/github/authenticating-to-github/testing-your-ssh-connection
https://docs.github.com/en/github/authenticating-to-github/error-permission-denied-publickey
https://jdblischak.github.io/2014-09-18-chicago/novice/git/05-sshkeys.html
I had already a key that I wanted to use. So adding it to the repo was ok.
Testing it was my challenge. I was missing two things. My key wasn’t following the standard file name so it wasn’t used by my ssh-agent and then, i wasn’t using the “git” user when testing…. I was using my github username.
So add the key and check it is there.
$ ssh-add ~/.ssh/id_ed25519-gh $ ssh-add -l -E md5 256 MD5:xx:xx:xx:xx:xx:67:xx:6a:73:xx:8a:xx:7f:78:xx:xx user@gh (ED25519)
Check you can ssh to github.
$ ssh -T git@github.com Hi xxxx! You've successfully authenticated, but GitHub does not provide shell access. $
Ok, all good now. But this is not a new repo, how I move from the “old” user/pass to the “new” ssh-key process?
You can clone the repo again using ssh:
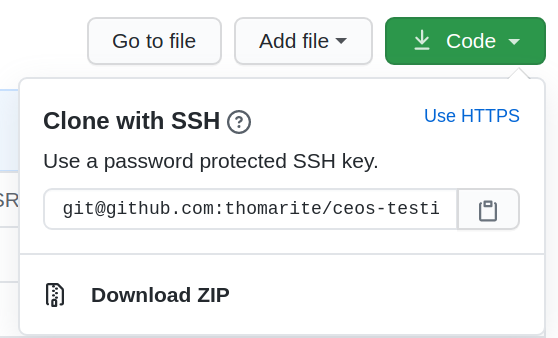
Or you can change the git config locally in the “url” bit.
/ceos-testing/.git master$ cat config [core] repositoryformatversion = 0 filemode = true bare = false logallrefupdates = true [remote "origin"] #url = https://github.com/thomarite/ceos-testing.git url = git@github.com:thomarite/ceos-testing.git fetch = +refs/heads/:refs/remotes/origin/ [branch "master"] remote = origin merge = refs/heads/master $
After that you can “git push” using your ssh-key.
2023-01
Looks like I dont learn the lesson….
1- Create Key
$ ssh-keygen -t ed25519 -C "your@email.com" Generating public/private ed25519 key pair. Enter file in which to save the key (/home/USERNAME/.ssh/id_ed25519): /home/USERNAME/.ssh/id_ed25519.github
2- Upload key to Github
3- Start agent and add key
$ ssh-agent -s SSH_AUTH_SOCK=/tmp/ssh-XXXXXXjMtZn7/agent.250293; export SSH_AUTH_SOCK; SSH_AGENT_PID=250294; export SSH_AGENT_PID; echo Agent pid 250294; $ ssh-add ~/.ssh/id_ed25519.github Identity added: /home/USERNAME/.ssh/id_ed25519.github (your@email.com) $
4- Authenticate to git
$ ssh -T git@github.com Hi USERNAME! You've successfully authenticated, but GitHub does not provide shell access. $
5- Push to git. Be sure your repo is not using https! Change it as showed here.
$ git remote get-url origin https://github.com/SOMEBODY/scripts.git $ git remote set-url origin git@github.com:SOMEBODY/scripts.git $ $ git remote get-url origin git@github.com:SOMEBODY/scripts.git $ $ git push Enumerating objects: 5, done. Counting objects: 100% (5/5), done. Delta compression using up to 4 threads Compressing objects: 100% (4/4), done. Writing objects: 100% (4/4), 2.07 KiB | 2.07 MiB/s, done. Total 4 (delta 1), reused 0 (delta 0), pack-reused 0 remote: Resolving deltas: 100% (1/1), completed with 1 local object. To github.com:SOMEBODY/scripts.git 6a4cb1a..07a4a83 main -> main $