Nothing to add. All is said:
https://as.com/baloncesto/2020/07/04/videos/1593850693_416569.html
Today I Learned
Nothing to add. All is said:
https://as.com/baloncesto/2020/07/04/videos/1593850693_416569.html
It is something I have never tried to bake. I consider it a very American/British thing. I have tried good ones in UK in Ben’s Cookies and it seems there is a great version in USA in Levain Bakery.
So searching for recipes, I chose this one:
Ingredients (adapted to what I have):
Plain flour 200g Self-Raising flour 100g 100% cocoa powder 50g 1 teaspoon of corn flour 1 teaspoon of baking soda 1 teaspoon of baking powder Half a teaspoon of salt Cold butter 200g Brown sugar 130g White sugar 70g 2 free range eggs - beaten room temperature 300g 80% dark chocolate in pieces 20g of mixed nuts crashed
Process:
Veredict
Obviously, they dont look like the ones in the video or the other sites but they were good.
Difficult to believe, but they dont taste super sweet. I used 100% cocoa powder and 85% dark chocolate. Still one cookie has the amount of chocolate and sugar that I take in one week 😛

Reminder
You can put the rest of cookies in the freezer! And enjoy fresh baked cookies any day!!! (I had three left over)
Mistakes
Another time, I will try the walnut one.
No, it is not me when I was a kid. It is a GC extension. I have a very bad habit of opening many tabs in my browser with the excuse, I will take a look later. That takes a big toll in CPU/Memory. With this extension, my laptop is running very smoothly even when I have three cEOS docker boxes running in the background. The fan runs less often. I have been using it for over a week and I am very happy with it. Need to find something for Firefox.
There are many links for this in the Internet so I am not going to discover the fire but I struggled a bit so….
The official links from github were ok and other people did a very good job too documenting the process.
https://docs.github.com/en/github/authenticating-to-github/testing-your-ssh-connection
https://docs.github.com/en/github/authenticating-to-github/error-permission-denied-publickey
https://jdblischak.github.io/2014-09-18-chicago/novice/git/05-sshkeys.html
I had already a key that I wanted to use. So adding it to the repo was ok.
Testing it was my challenge. I was missing two things. My key wasn’t following the standard file name so it wasn’t used by my ssh-agent and then, i wasn’t using the “git” user when testing…. I was using my github username.
So add the key and check it is there.
$ ssh-add ~/.ssh/id_ed25519-gh $ ssh-add -l -E md5 256 MD5:xx:xx:xx:xx:xx:67:xx:6a:73:xx:8a:xx:7f:78:xx:xx user@gh (ED25519)
Check you can ssh to github.
$ ssh -T git@github.com Hi xxxx! You've successfully authenticated, but GitHub does not provide shell access. $
Ok, all good now. But this is not a new repo, how I move from the “old” user/pass to the “new” ssh-key process?
You can clone the repo again using ssh:
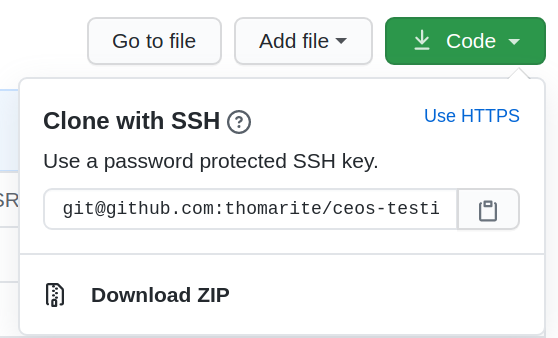
Or you can change the git config locally in the “url” bit.
/ceos-testing/.git master$ cat config [core] repositoryformatversion = 0 filemode = true bare = false logallrefupdates = true [remote "origin"] #url = https://github.com/thomarite/ceos-testing.git url = git@github.com:thomarite/ceos-testing.git fetch = +refs/heads/:refs/remotes/origin/ [branch "master"] remote = origin merge = refs/heads/master $
After that you can “git push” using your ssh-key.
2023-01
Looks like I dont learn the lesson….
1- Create Key
$ ssh-keygen -t ed25519 -C "your@email.com" Generating public/private ed25519 key pair. Enter file in which to save the key (/home/USERNAME/.ssh/id_ed25519): /home/USERNAME/.ssh/id_ed25519.github
2- Upload key to Github
3- Start agent and add key
$ ssh-agent -s SSH_AUTH_SOCK=/tmp/ssh-XXXXXXjMtZn7/agent.250293; export SSH_AUTH_SOCK; SSH_AGENT_PID=250294; export SSH_AGENT_PID; echo Agent pid 250294; $ ssh-add ~/.ssh/id_ed25519.github Identity added: /home/USERNAME/.ssh/id_ed25519.github (your@email.com) $
4- Authenticate to git
$ ssh -T git@github.com Hi USERNAME! You've successfully authenticated, but GitHub does not provide shell access. $
5- Push to git. Be sure your repo is not using https! Change it as showed here.
$ git remote get-url origin https://github.com/SOMEBODY/scripts.git $ git remote set-url origin git@github.com:SOMEBODY/scripts.git $ $ git remote get-url origin git@github.com:SOMEBODY/scripts.git $ $ git push Enumerating objects: 5, done. Counting objects: 100% (5/5), done. Delta compression using up to 4 threads Compressing objects: 100% (4/4), done. Writing objects: 100% (4/4), 2.07 KiB | 2.07 MiB/s, done. Total 4 (delta 1), reused 0 (delta 0), pack-reused 0 remote: Resolving deltas: 100% (1/1), completed with 1 local object. To github.com:SOMEBODY/scripts.git 6a4cb1a..07a4a83 main -> main $
I have realised that I had two keys in my VPS and I wasn’t sure which one it was used when I was ssh-ing so I had to search a bit to find out.
These two links cover the process:
1- You need to increase the logging of your sshd (destination – server)
server# vim /etc/ssh/sshd_config LogLevel VERBOSE server# service sshd restart server# tail -f /var/log/auth.log
2- From client, just ssh as usual to the server and check auth.log as per above
Jul 3 14:17:55 server sshd[8600]: Connection from IPV6 port 57628 on IPV6::453 port 64022 Jul 3 14:17:55 server sshd[8600]: Postponed publickey for client from IPv6 port 57628 ssh2 [preauth] Jul 3 14:17:55 server sshd[8600]: Accepted publickey for client from IPv6 port 57628 ssh2: ED25519 SHA256:BtOAX9eVpFJJgJ5HzjKU8E973m+MX+3gDxsm7eT/iEQ Jul 3 14:17:55 server sshd[8600]: pam_unix(sshd:session): session opened for user client by (uid=0) Jul 3 14:17:55 server sshd[8600]: User child is on pid 8606 Jul 3 14:17:55 server sshd[8606]: Starting session: shell on pts/7 for client from IPv6 port 57628 id 0
3- So we have the fingertip of the key used by client. Now we need to get the fingertips of our clients keys to find the match:
client $ ssh-keygen -l -f ~/.ssh/id_ed25519.pub 256 SHA256:BtOAX9eVpFJJgJ5HzjKU8E973m+MX+3gDxsm7eT/iEQ client@local (ED25519)
4- So the we can see that I am using my id_ed25519.pub key to connect to the server
Nornir is a python framework mainly for network automation. Instead of using another tool like Ansible (that you need to learn), you can do the same just using pure python all the way. Ansible doesnt scale well and can be very slow, with nornir you have threading from day zero, so if you have to run tasks in 100 devices, you will feel and see the difference.
I learnt about nornir via Kirk Byers’ course. Unfortunately I didnt have the chance/time to use it in my former day job so now I have had time to review things and do a small project.
From https://github.com/thomarite/ceos-testing in the nornir section you can find the whole environment. I tested on the 3-node topology.
It is nothing special. The script builds the config for BGP or ISIS using jinj2 and yaml files. I have the feeling that my jinja2 is a bit difficult to follow. Then using napalm connects to the devices to push or check the config.
Just one issue, as it seems due to the nature of cEOS relaying on docker and my filesystem, if you decide to push the config (dry_run=False == commit=True) the task will fail (while trying to write startup config) but it is actually executed.
(testdir2) /testdir2/ceos-testing/nornir master$ python buid-config.py -b isis -c hostname: r1 task: deploy_config for isis failed: True logs: Traceback (most recent call last): ... File ".../testdir2/lib/python3.7/site-packages/pyeapi/eapilib.py", line 469, in send raise CommandError(code, msg, command_error=err, output=out) pyeapi.eapilib.CommandError: Error [1000]: CLI command 5 of 5 'write memory' failed: could not run command [Error copying system:/running-config to flash:/startup-config (Operation not permitted)] changed: False diff: hostname: r2 task: deploy_config for isis failed: False logs: None changed: False diff: hostname: r3 task: deploy_config for isis failed: False logs: None changed: False diff:
This shouldn’t happen on vEOS or the real hardware (if you have the correct aaa config of course)
Reflect:
client -> clients and non-clients
non-client -> clients
No Reflect:
non-client -> no-client (normal ibgp)
always advertises to eBGP peers (normal ebgp)
eBGP learned prefixes, advertised to client and non-clients (normal ebgp)
Full Mesh iBGP:
Reflects ONLY the best route
RRs dont modify on reflected routes: NEXT_HOP, AS_PATH, LP and MED.
Prevent routing information loops: ORIGINATOR_ID and CLUSTER_LIST
Clustering:
Hierarchical Route Reflection: 2 levels: - level1 RRs are clients of level2 RR -> level1 RR dont need full mesh between them - level2 RRs are full mesh between them. Consider: size of top-level mesh number of alternative paths
Hierarchical Route Reflection:
2 levels:
– level1 RRs are clients of level2 RR -> level1 RR dont need full mesh between them
– level2 RRs are full mesh between them.
Consider:
RR Design Priciples:
It is something I have watched from several sites and finally noticed a page that mentioned how was done.
So this is the tool: https://asciinema.org/
And this is an example I have recorded. I have just to create a HTML entry and copy the code.
Summary:
$ python -m pip install asciinema $ asciinema rec /// or /// python -m asciiema rec asciinema: recording asciicast to /tmp/tmpvjba98p7-ascii.cast asciinema: press or type "exit" when you're done ... $ exit exit asciinema: recording finished asciinema: press to upload to asciinema.org, to save locally asciinema: asciicast saved to /tmp/tmphxkq5sp2-ascii.cast $ asciinema upload /tmp/tmphxkq5sp2-ascii.cast
Template for getting a basic Debian VM with python virtualenv and pyenv. Run python3 by default
$ sudo aptitude update
$ sudo aptitude dist-upgrade
$ sudo apt-get install -y python3-pip
$ sudo apt install git
$ sudo adduser --home /home/USER --shell /bin/bash USER
$ sudo usermod -a -G sudo USER
$ vim .bashrc
#
Python configuration
#
pyenv
https://github.com/yyuu/pyenv
git clone https://github.com/yyuu/pyenv.git ~/.pyenv
git clone https://github.com/yyuu/pyenv-virtualenvwrapper.git ~/.pyenv/plugins/pyenv-virtualenvwrapper
virtualenvwrapper
http://virtualenvwrapper.readthedocs.org/en/latest/
export PYENV_ROOT="$HOME/.pyenv"
export PATH="$PYENV_ROOT/bin:$PATH"
if [ ! -d "$PYENV_ROOT" ];then
git clone https://github.com/pyenv/pyenv.git ~/.pyenv
fi
if [ ! -d "$PYENV_ROOT/plugins/pyenv-virtualenvwrapper" ]; then
mkdir -p $PYENV_ROOT/plugins
git clone https://github.com/yyuu/pyenv-virtualenvwrapper.git $PYENV_ROOT/plugins/pyenv-virtualenvwrapper
fi
if type "pyenv" &> /dev/null; then
eval "$(pyenv init -)"
# TODO: make the prompt work for python and ruby
__pyversion (){
if type "python" > /dev/null; then
pyenv_python_version=$(pyenv version | sed -e 's/ .*//')
printf $pyenv_python_version
fi
}
if pyenv which pip &> /dev/null; then pyenv virtualenvwrapper fi export PS1="py:\$(__pyversion)|$PS1"
fi
export PROJECT_HOME=~/git
export PYTHONDONTWRITEBYTECODE=1
end python
$ bash
$ sudo apt-get install -y --no-install-recommends make build-essential libssl-dev zlib1g-dev libbz2-dev libreadline-dev libsqlite3-dev wget curl llvm libncurses5-dev xz-utils tk-dev libxml2-dev libxmlsec1-dev libffi-dev liblzma-dev tcpdump tree
$ pyenv install 3.7.3
$ pyenv global 3.7.3
I had my shiny and tiny GCP network for EVE-NG to test vEOS. I built a new VM (vm2) to be my center for automation so I can test stuff like ansible/napalm/nornir etc… But I couldn’t ping from vm2 to the vEOS instances in eve-ng (vm1). Those instances where in a different network attached to vm1 so it had to “route”.
As usual, I missed one step when I created the EVE-NG VM. The official documentation doesnt mention anything regarding enabling routing in the VM. As I am not used to Cloud environments, I assume that any simple Linux VM can forward traffic if configured.
Surprise Surprise. In GCP (not sure in other cloud providers), you need to enable “forwarding” during the VM creation and you can’t change that afterwards in any way.
After checking the second guide I followed, I realised that guide mentioned the point to enable forwarding to avoid the same problem I was facing…
So I had to gave up and had to build both VMs from scratch….
But at the end, I have routing enabled in both VMs and I can ping to the vEOS images.
And another annoying thing. I couldnt update the next hop in a static route defined in the VPC. So I had to delete it and create again pointing to the new VM with the vEOS.
And dealing with the internal IPs…
Moving on, quite frustrating day. But learned several things about GCP netwoking.